Blockchain vs. Traditional Databases: What’s the Difference
Blockchain technology has revolutionized the way we store and manage data, challenging the traditional databases that have been in use for decades. The fundamental difference lies in the approach to data structure and the centralization versus decentralization of authority.
Corblocks Team, Blockchain experts, domain specialists, tailored DLT solutions, industries, sectors, peer-to-peer transactions, faster, transparent, secure, Blockchain development service.
By leveraging the power of DLT technology such as Blockchain, we can streamline your business operations by eliminating intermediaries and reducing transaction times. Our tailored DLT solutions ensure transparency by providing an immutable record of all transactions on the network. Moreover, with advanced encryption techniques and consensus algorithms in place – you can rest assured that your data is secure from unauthorized access or tampering
Here’s a comparison Blockchain vs. Traditional Databases:
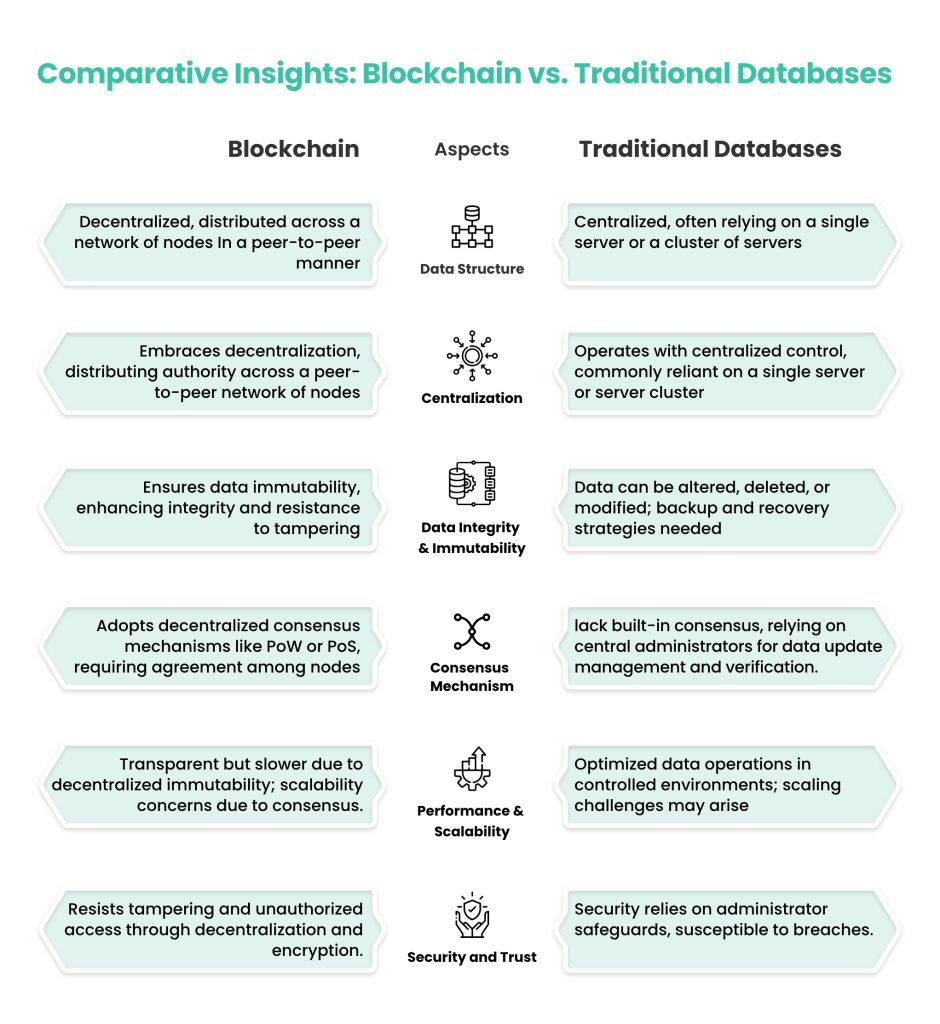
1. Centralization vs. Decentralization:
• Blockchain: A blockchain is a distributed, decentralised digital ledger that keeps track of transactions between several computers, or “nodes.” It does away with the requirement for a central authority and enables several parties to jointly manage and validate the database.
• Traditional Database: Traditional databases are controlled by a single institution or organization that is centrally located. To manage access and adjust, they need a central administrator.
2. Data Structure:
• Blockchain: Each block of data in a blockchain contains a collection of transactions. A chain of blocks is created by connecting these blocks in reverse chronological order.
• Traditional Database: Different data models, including relational (tables with rows and columns), NoSQL (document, key-value, graph, etc.), or NewSQL (enhanced relational databases), are used by traditional databases. 
3. Immutability:
• Blockchain: A blockchain makes it nearly impossible to change or remove data once it has been added. Consensus techniques and cryptographic hashing are used to accomplish this immutability.
• Traditional Database: Traditional databases allow for the simple modification or deletion of data by authorised users with the appropriate permissions.
4. Consensus Mechanism:
• Blockchain: To validate and reach consensus on the ledger’s current state across nodes, blockchains rely on consensus procedures (such as Proof of Work and Proof of Stake). Without relying on a centralised authority, this maintains data integrity.
• Traditional Database: Traditional databases lack built-in consensus procedures by nature. The management and verification of data updates is left to the central administrator.
5. Security and Trust:
• Blockchain: Blockchain is resistant to tampering and unauthorised access due to its decentralised structure and encryption measures.
• Traditional Database: Security depends on the safeguards put in place by the database administrator, which can be breached.
6. Performance and Scalability:
• Blockchain: Due to the distributed nature and consensus methods, blockchains can have scalability problems that make them slower for high-throughput applications.
• Traditional Database: When it comes to performance and scalability, traditional databases frequently perform better for applications that need quick data processing.
Use Cases:
• Blockchain: Supply chain management, provenance monitoring, and digital identity verification are a few examples of applications where blockchain is frequently
appropriate. These scenarios call for transparency, traceability, and responsibility.
• Traditional Database: For many applications, including content management systems (CMS), customer relationship management (CRM), and financial transactions, traditional databases are frequently employed.
In conclusion, while traditional databases offer efficiency and performance advantages in certain scenarios, blockchain technology brings decentralization, immutability, and transparency to the table. Understanding these differences can help businesses determine which solution best suits their specific needs for secure and reliable data management.